The fastest and
most advanced
data protection
Control, protect, collaborate and process your data with solutions that can outperform all competitors on the market.
Control, protect, collaborate and process your data with solutions that can outperform all competitors on the market.
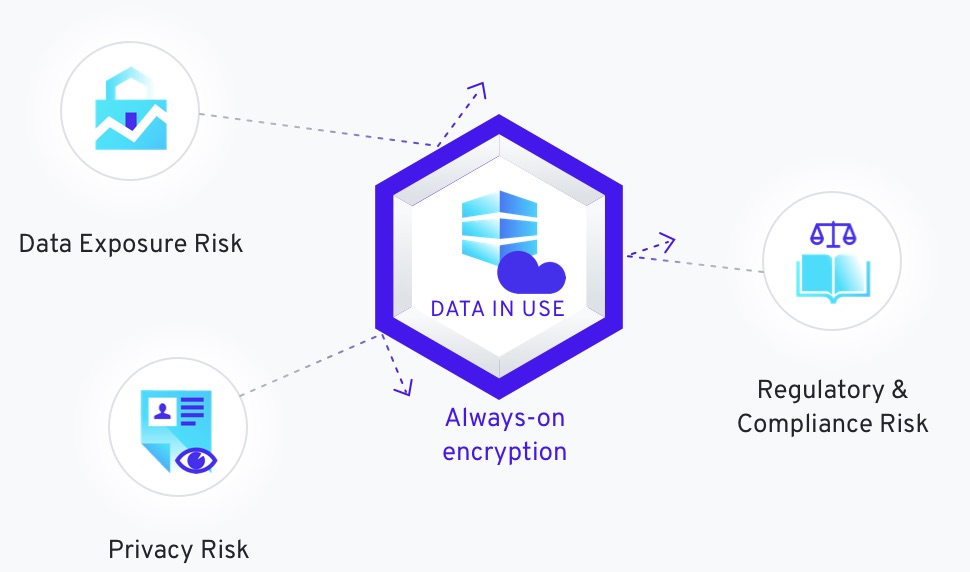
Our products offer a higher level of privacy and security for your customers. By encrypting all data-in-use we add another layer of protection, and allow for usage of data without the additional expense of anonymization, or the problem of operators of systems having access to the data that resides there.


We’ve made controlling the access with specific keys and controls easy and fast. Moreover, by design our applications keep the keys and the data separate, rendering the data unusable even for those with direct access to the data store.
With Eaglys solutions data can be exchanged without running afoul of regulations or privacy concerns. Moreover, the knowledge contained within data sets can also be made available as a service to your clients, who can submit encrypted queries against your data and decrypt the results with the keys you provide.

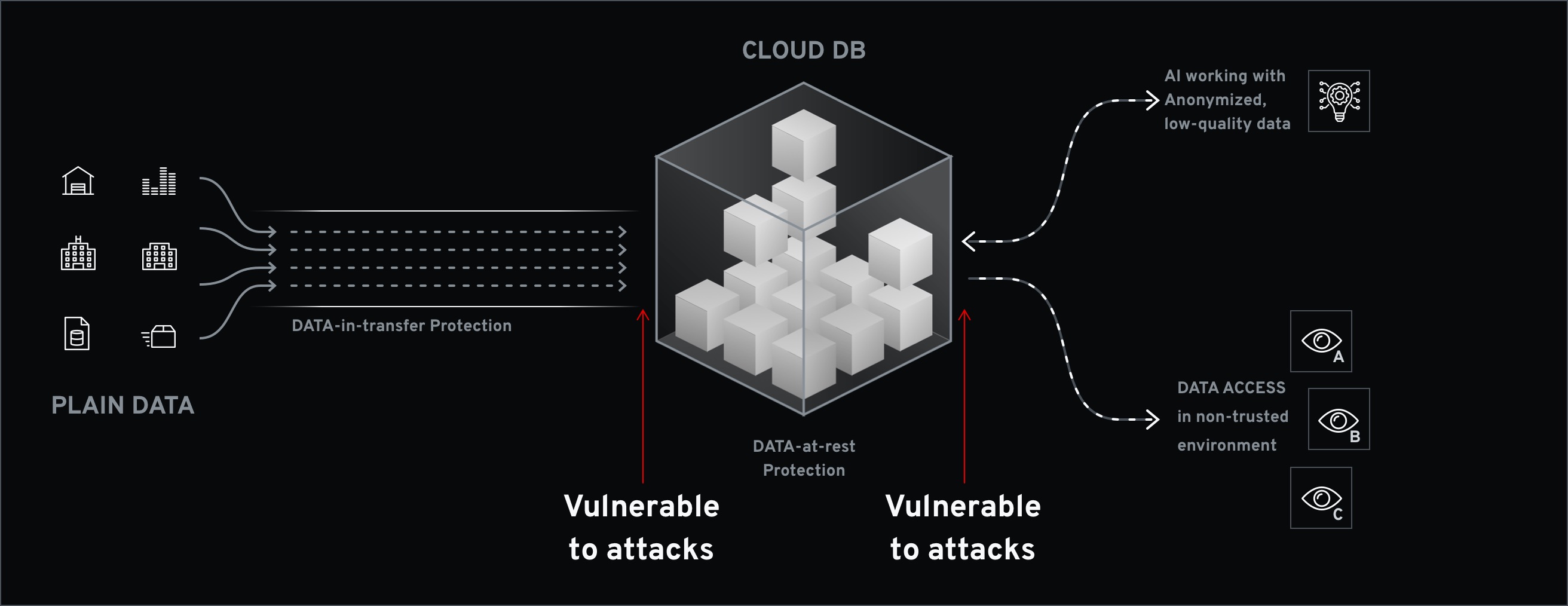
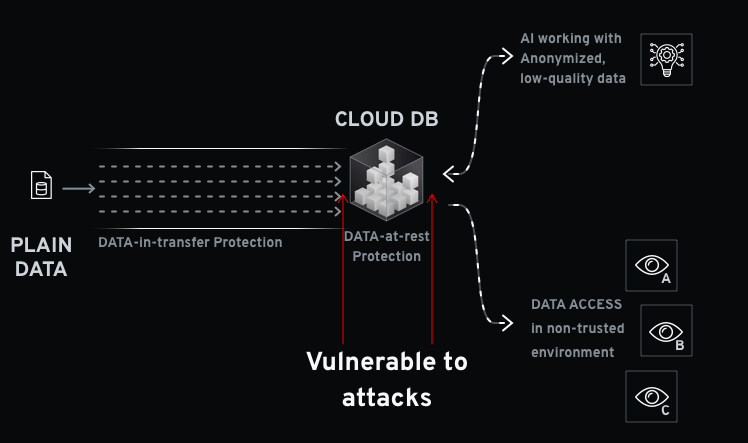
DataArmor focuses on encrypting all of your data, not only in transit or at rest but also in use. This ensures your data is always safe, no matter where it is being processed. Existing approaches to protecting network traffic or servers do not prevent data leak incidents which result from errors in operation, architectural design, or configuration. The only true solution is operations over always-encrypted data.
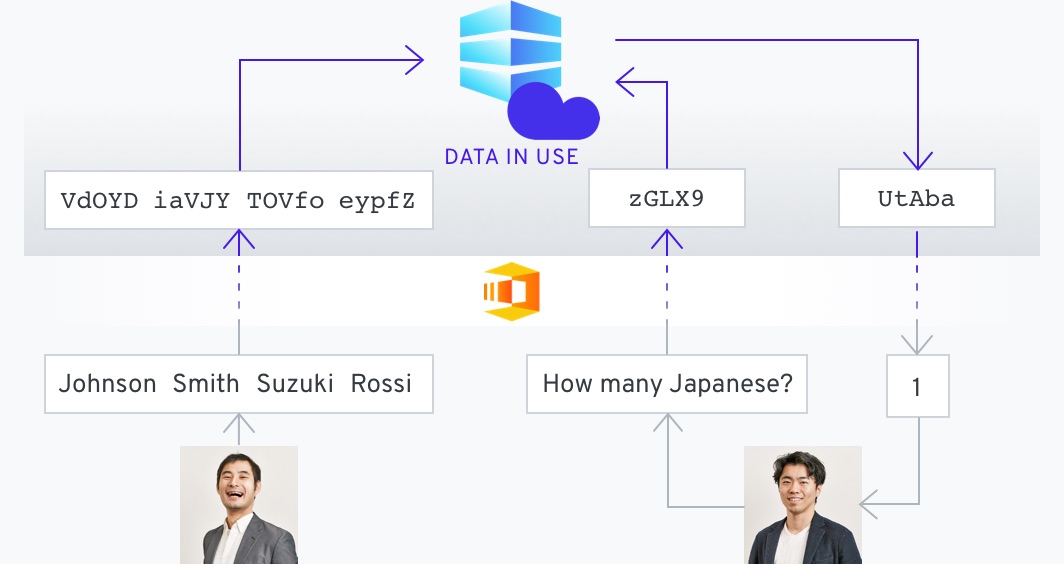
Secure computing technology enables you to exchange knowledge, and connect with partners without the necessity of revealing the confidential information within. Collaborate with your industry peers without revealing your secrets. And, as the data is always encrypted, gain your customers’ confidence in sharing their data.
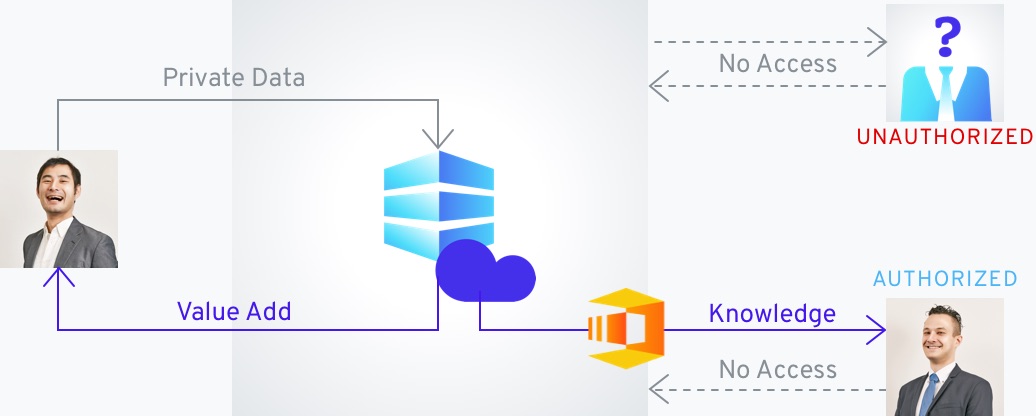
Process your customer’s data in an always encrypted, and privacy preserving format, protecting their information and ensuring compliance with internal as well as external regulations.
1.
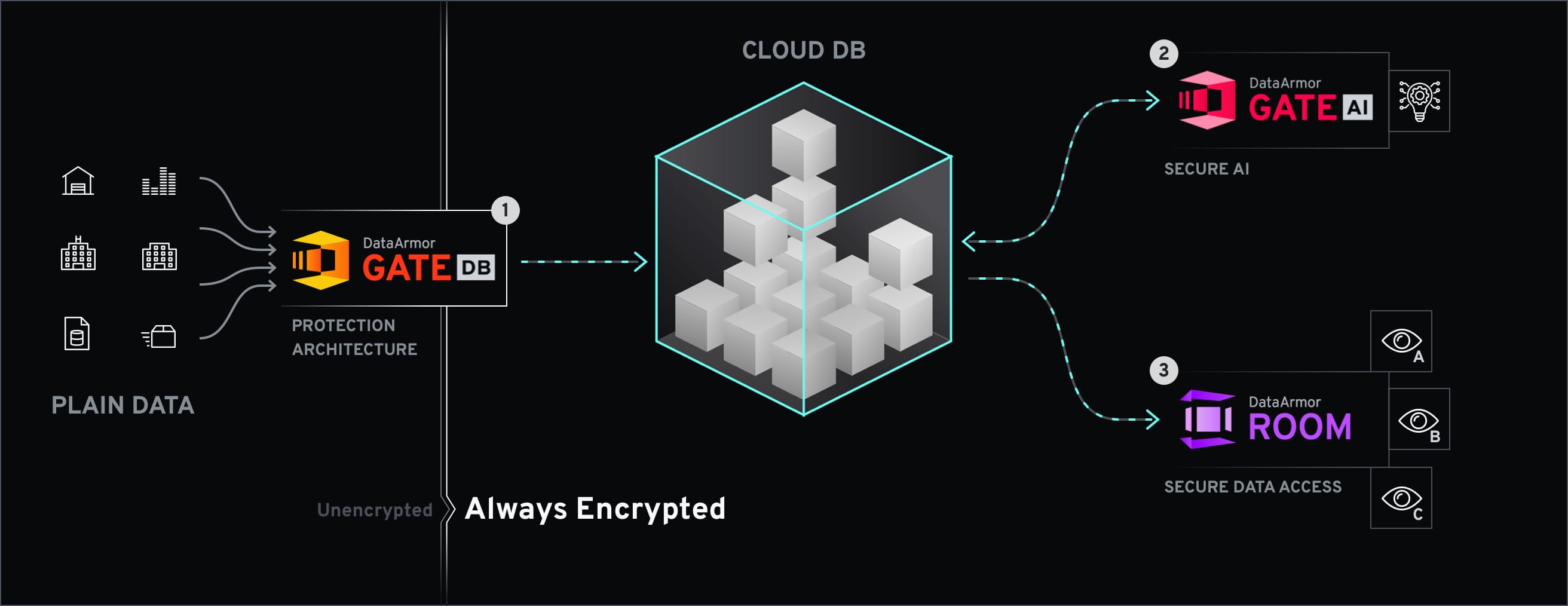
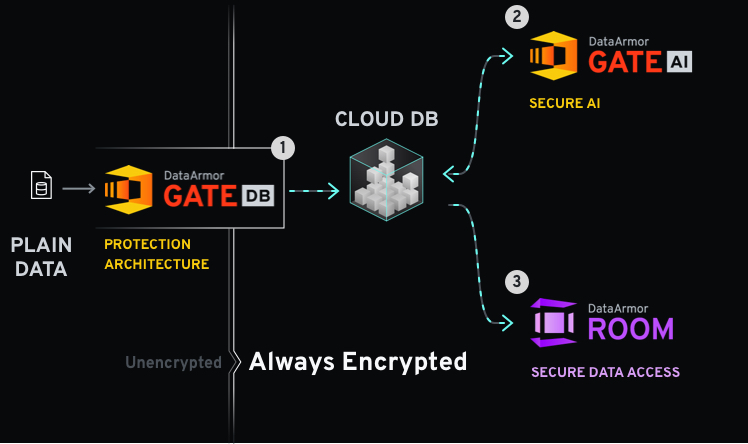
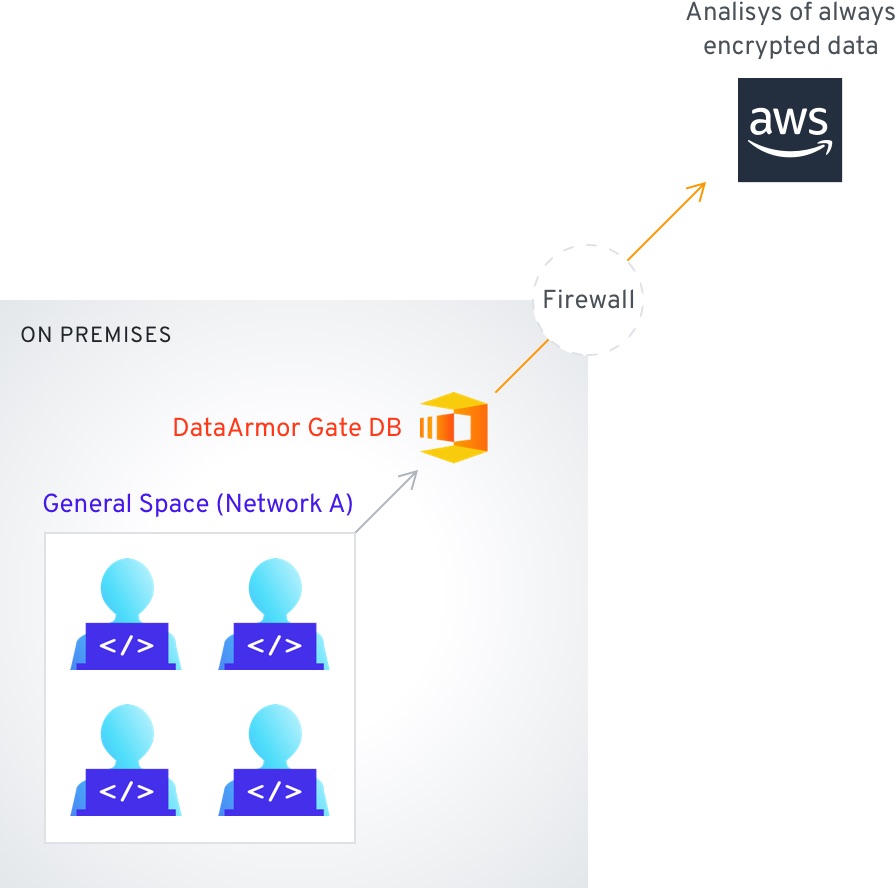
DataArmor Gate DB is a turn key solution for always on encryption of databases that contain highly sensitive data or operate in non-trusted zones such as the cloud. The contents of the databases are encrypted and all queries are performed over encrypted data only. The encryption keys are stored separately from the database, and data is never decrypted at the database side. This is in contrast to current database solutions which partially decrypt the data when performing queries.
Learn more about GateDB2.
DataArmor Gate AI allows for encryption of Ai models as well as utilization of AI models with encrypted data, allowing them to take advantage of secure computing. We are currently implementing this functionality on a project basis, and developing a drop in solution for existing systems. This makes it possible to, for example, execute predictions over the a counterpart's (customers, business partners, etc.) dataset without revealing the AI model itself – it can also enable the use of shared models and datasets. Moreover, when combined with DataArmor Gate DB you can perform AI operations over encrypted databases. Namely, encrypted data retrieved from database is directly inputing to encrypted machine learning model to obtain predicted results.
Learn more about GateAI3.
DataArmor Room, our latest project, is a service to allow data scientists and other authorized users partial access to secure data – access that may be necessary for the development of AI model, audits, compliance assurance, etc. This solution takes a multi-tiered approach, merging encryption technologies with strict access control to provide a safe, secure, and useful data access environment.
Learn more about RoomYou don’t have to build your own secure environment from scratch. Enabling the DataArmor driver or connecting via the API your existing system can be quickly made secure.
Through an in-depth investigation of your requirements, our team of engineers will map the requirements to your business needs, create your solution, and offer flexible support.
Reduce the development and operations costs that a secure system would require. Start saving on monitoring, security, risk management and more.
(Coming soon) Discover more about installation on our Github documentation
Discover the different scenarios in which EAGLYS’ DataArmor solutions can revolutionize industries and businesses that work with data.
The analysis of very sensitive data may require additional security and access controls, as well as prevent full use of cloud computing. However, with the use of secure computing the data can be stored off-site while the keys can be tightly controlled on-site. This allows for a stricter access control via key management, as well as obviates some of the need for additional parallel systems to store and handle said confidential data during analysis.
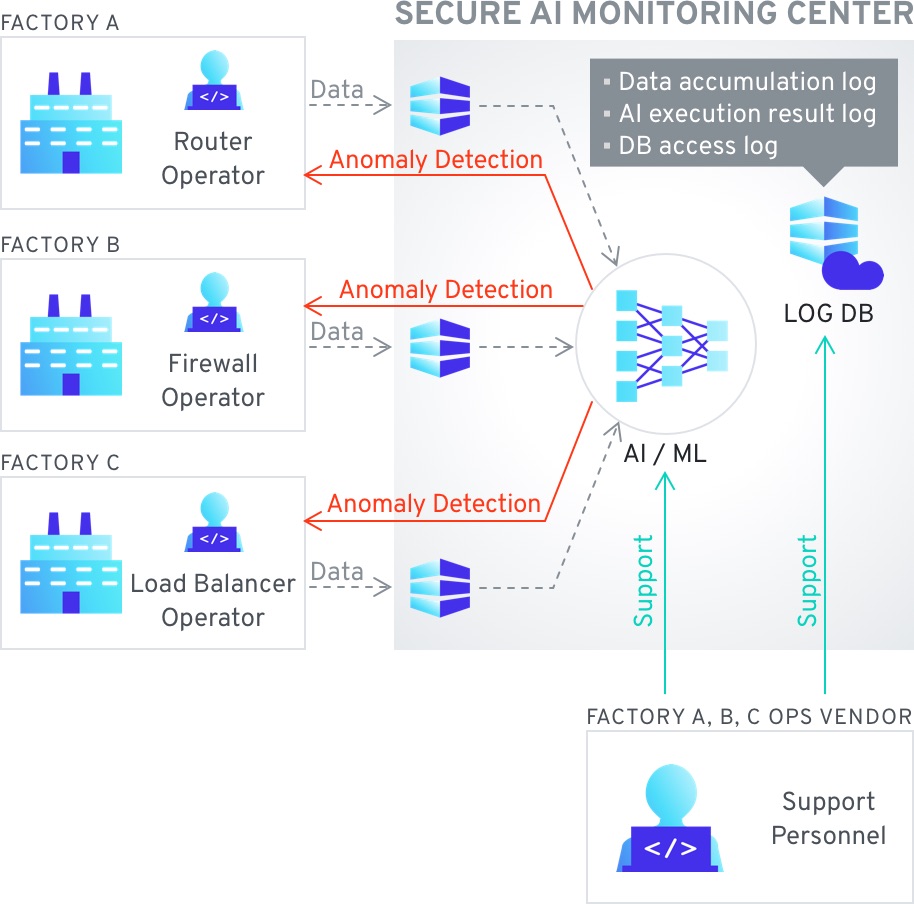
This use case concerns manufacturing statistical data, sourced from automation systems or IoT systems within the factory, providing information on performance, production output, logistics, etc. This data might need to be useable within the factory For any system that has to analyze and adjust operations autonomously. The specific drivers of this use case are security of the data in cases where the factory may not be in a completely Secure area, or the staff at the factory must not have access to detailed information – while the automated system needs the ability to calculate said data. One example of problems caused by access by wrong parties is the potential to predict the performance of a company ahead of earnings reports based on factory performance data.
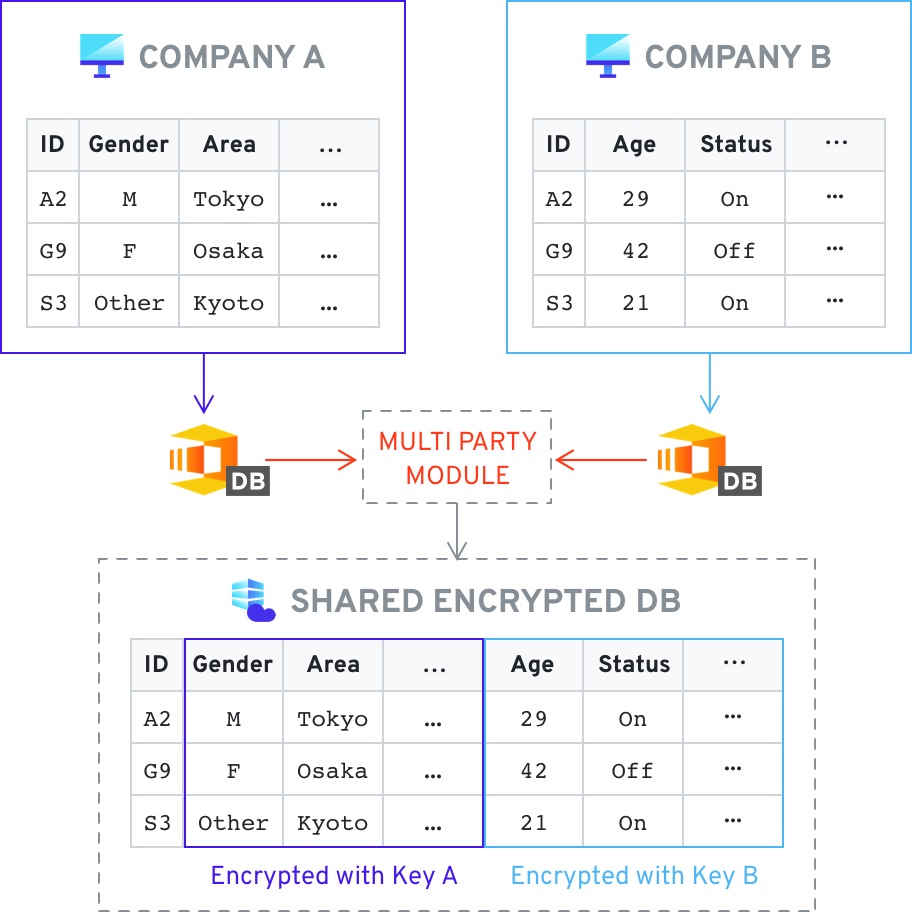
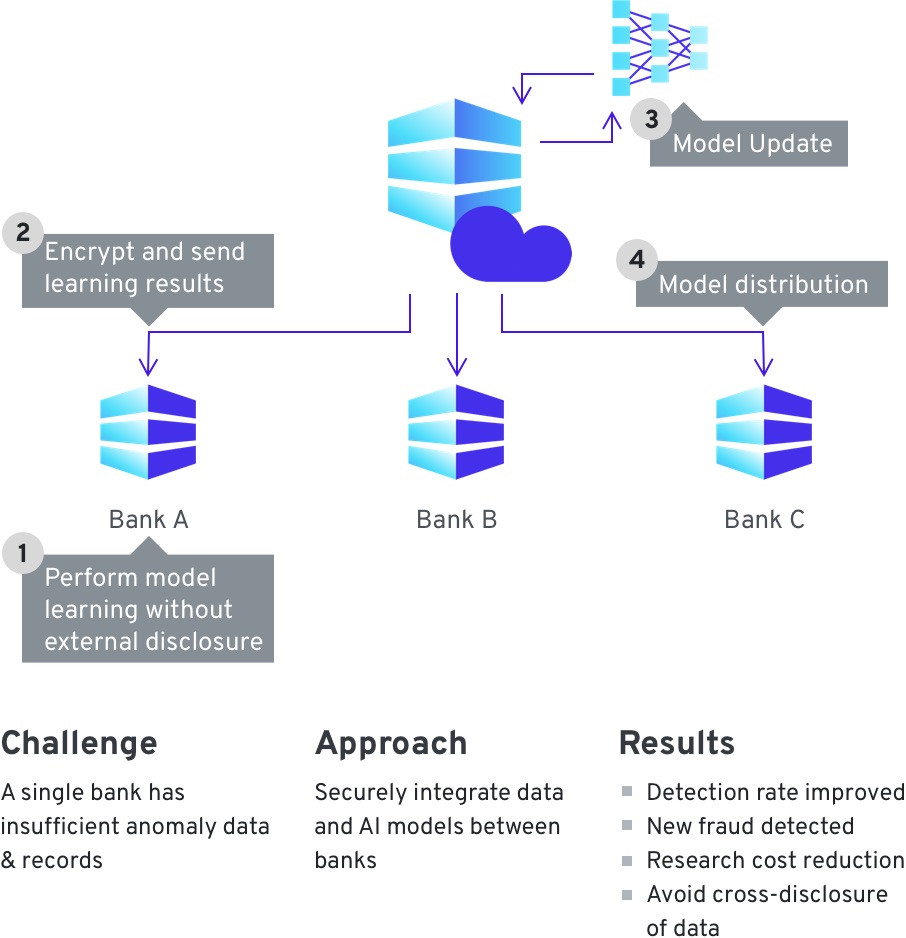
In this use case two different data sets can be merged using two separate keys, and stored in a central location, for example the cloud. Once the data is combined the entities can analyze the combined data without revealing the underlying information. This is extremely useful in cases such as fraud detection, where companies want to be able to analyze customer data for fraudulent activity, specific behavior patterns, or other flags - all without revealing the specific customer entries.

Each DataArmor Gate DB does not allow other parties (even platform providers) to access its data inside.
Each decryption key is only used in its specific DataArmor GateDB and no other party has access to it.
Enabling fraud detections through organizations exchanging information on fraudulent transactions. The data, if exchanged in an unencrypted format, has to be obfuscated and sanitized of all private data – rendering any models built on this basis far less accurate. By using secure computing solutions, entities can exchange their data as encrypted, and run analysis directly over the encrypted data – never accessing the customer information directly. This allows them to find anomalies and create accurate machine learning models that can detect such anomalies over their internal customer data – or request keys to decrypt specific portions of the data set as needed. This makes faster and more accurate detection and prevention of fraud possible.
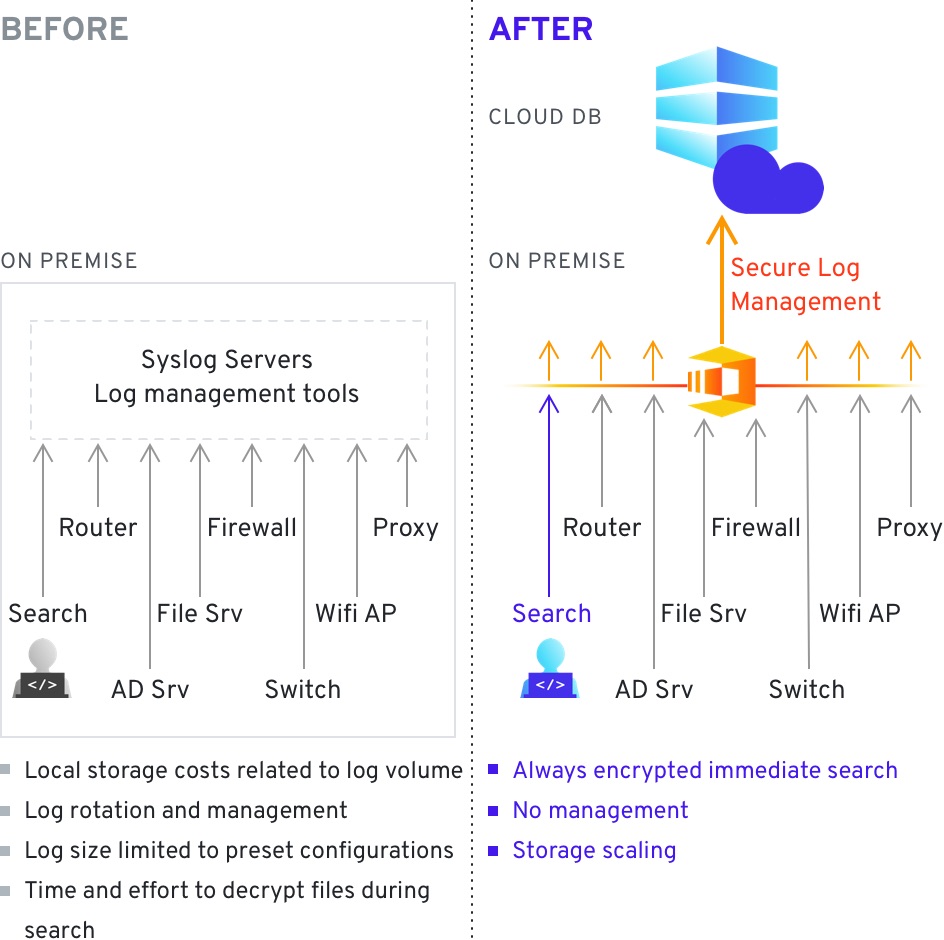
Secure computing can help in the aggregation of logs from various systems and IoT devices – as any system can encrypt and upload data into the cloud, without the possibility of the cloud service provider having any access to the data itself. While the data cannot be decrypted in the cloud it can be analyzed and transformed – allowing for the use of cloud computing resources and storage for sensitive log data while guaranteeing safety and confidentiality. This is especially important in cases where data needs to be centralized but logs may contain private or sensitive information such as account numbers, credit card numbers, etc. With secure computing both the ease of use and the confidentiality of the data is taken into account.
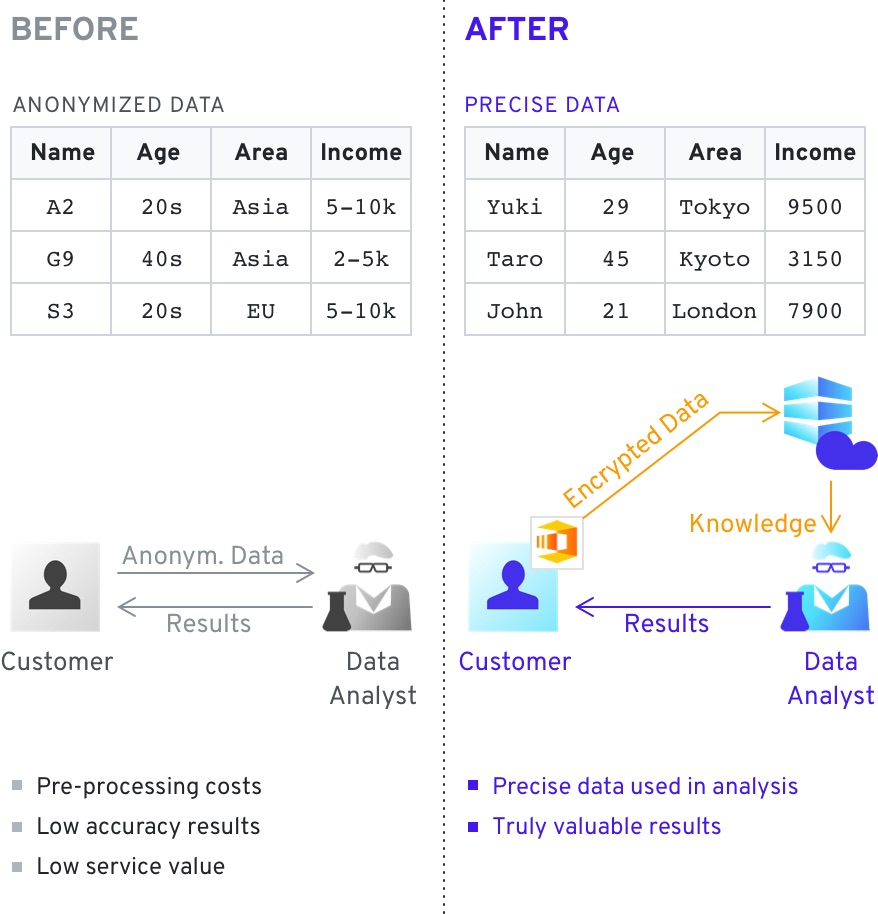
In cases where sensitive Human Resources information is outsourced to a vendor, data would often need to be obfuscated due to regulations and privacy considerations. However, with secure computing the data can be provided as an encrypted blob – completely unreadable however still allowing the 3rd party to perform analysis and apply specific computations as needed. Both the original and the resultant data is always encrypted and the 3rd party never has access to the underlying information – however their ability to fulfill their obligations is preserved.
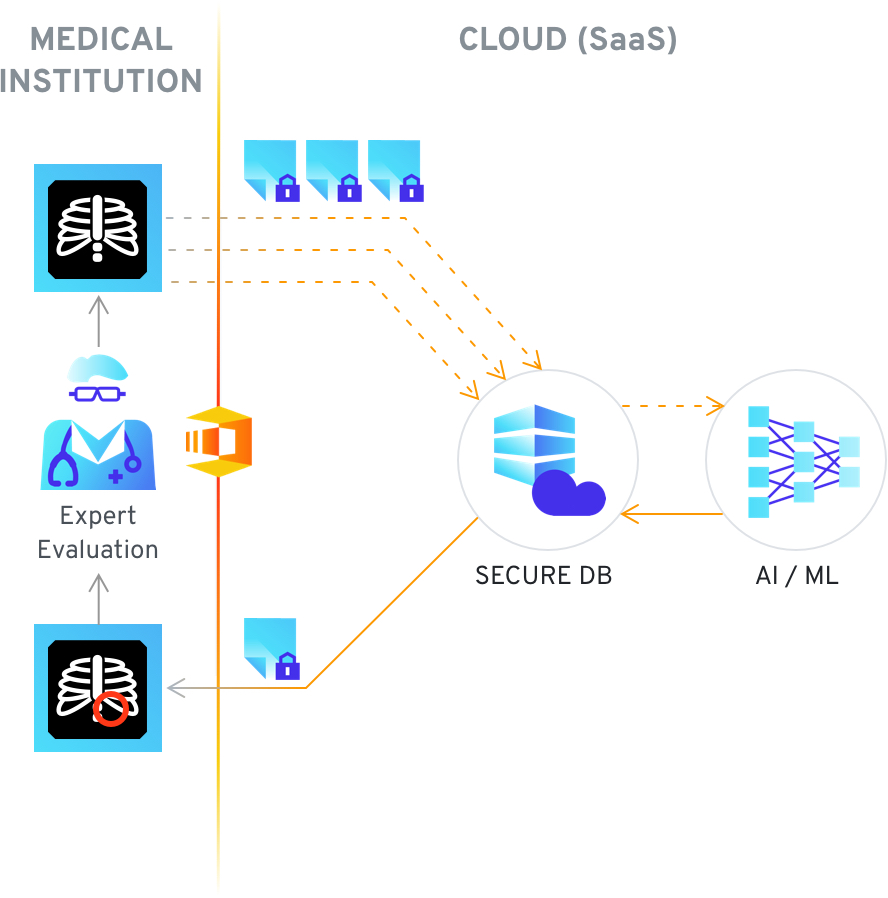
Secure computing can help in the training of AI to detect anomalies in medical image data – as generally large data sets are required, while a single medical provider can produce a limited volume of said data. This results in insufficient data being available to create AI models to detect anomalies, as well as some limitations on providing services where patient data would be processed. The problem can be mitigated by the use of secure computing, where patient data would be encrypted and processed only in an encrypted format. This allows for access to a far wider scope of patient records, as well as opens the opportunity to provide the same anomaly detection as a service. Encrypted patient data can be both analyzed for anomalies as well as used for the improvement of the AI model, whereas it can only be decrypted by the originator of the data.
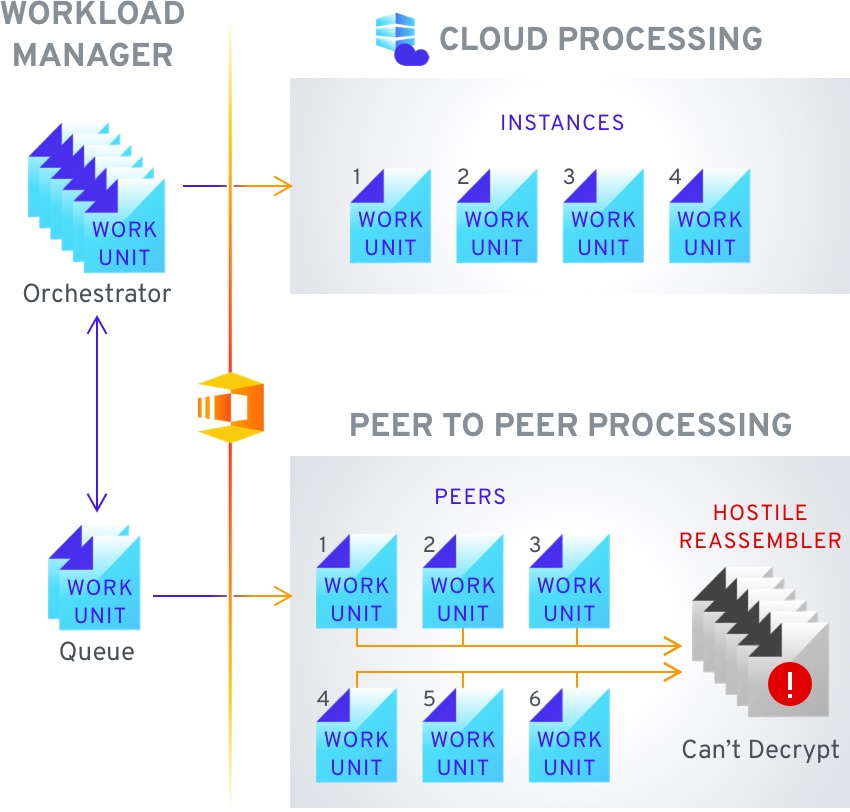
Secure computing increases the security of Peer2Peer assisted computing, where processing is split up between the cloud and various peers. If the data is processed while unencrypted, any peer has access to a component of the data. What is more critical is if an attacker compromises enough peers or gains the ability to redirect work units to specific nodes – if enough work units are collected the attacker can then start reconstructing the original data, filling in the gaps via inference. With the use of secure computing technologies this becomes impossible as all data is processed in an encrypted state and the peers never have access to the keys. Only the workload manager has access to the keys and is able to decrypt the data, while any attackers are left holding only fragments of the encrypted data without any way of decrypting it.
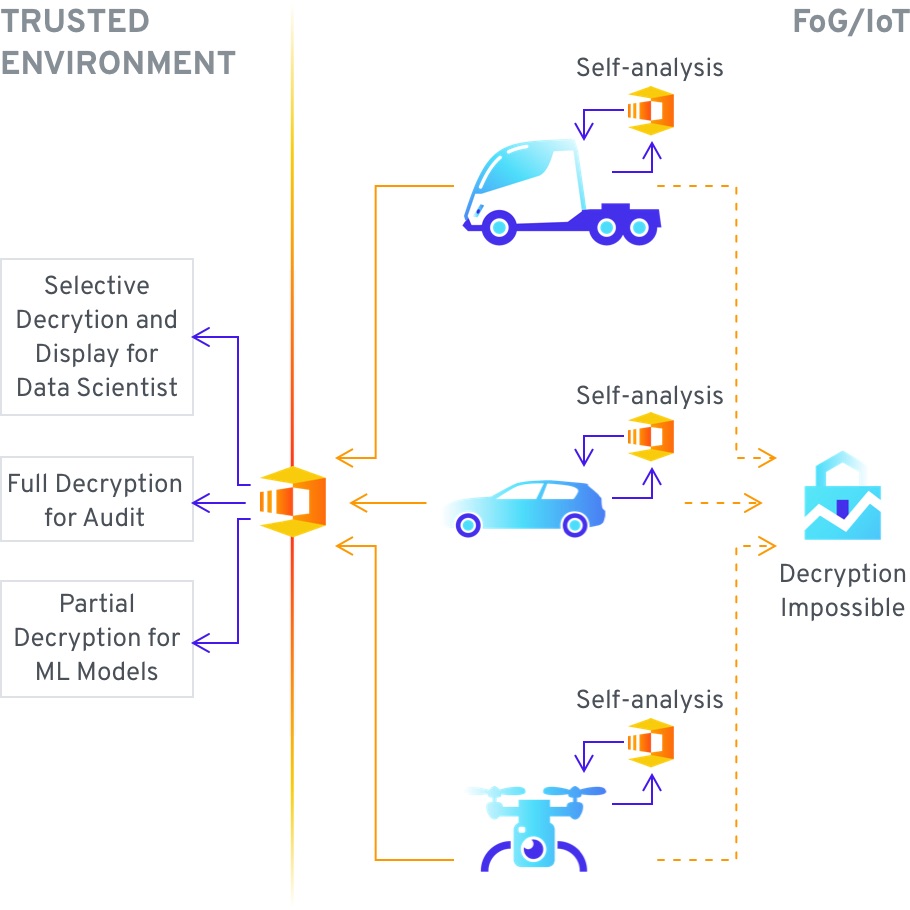
Secure computing can protect the data stored on vehicles which is aggregated from the onboard sensors – to enable such functionality as predicting necessary maintenance intervals or inferring the operational capabilities of the vehicle. This data needs to be protected as oftentimes it contains location data, and with sufficient resolution it can be used to infer the behavior of the owner, approximation of who is traveling in the vehicle, and the general scope of activities. As the data is necessarily stored on the vehicle itself, if it is not encrypted it can be easily accessed during a visit to the mechanic, or even maliciously by anyone that can gain physical access to said vehicle. With the use of secure computing the data can be encrypted, and live on the vehicle only in that format. The vehicle ML models can still operate over the encrypted data but the data cannot be decrypted while it is in use. The data can also be uploaded to a central location in the cloud or on company servers, and processed as an aggregate of a vehicle fleet, decrypted as needed for further analysis or simply kept for compliance reasons.