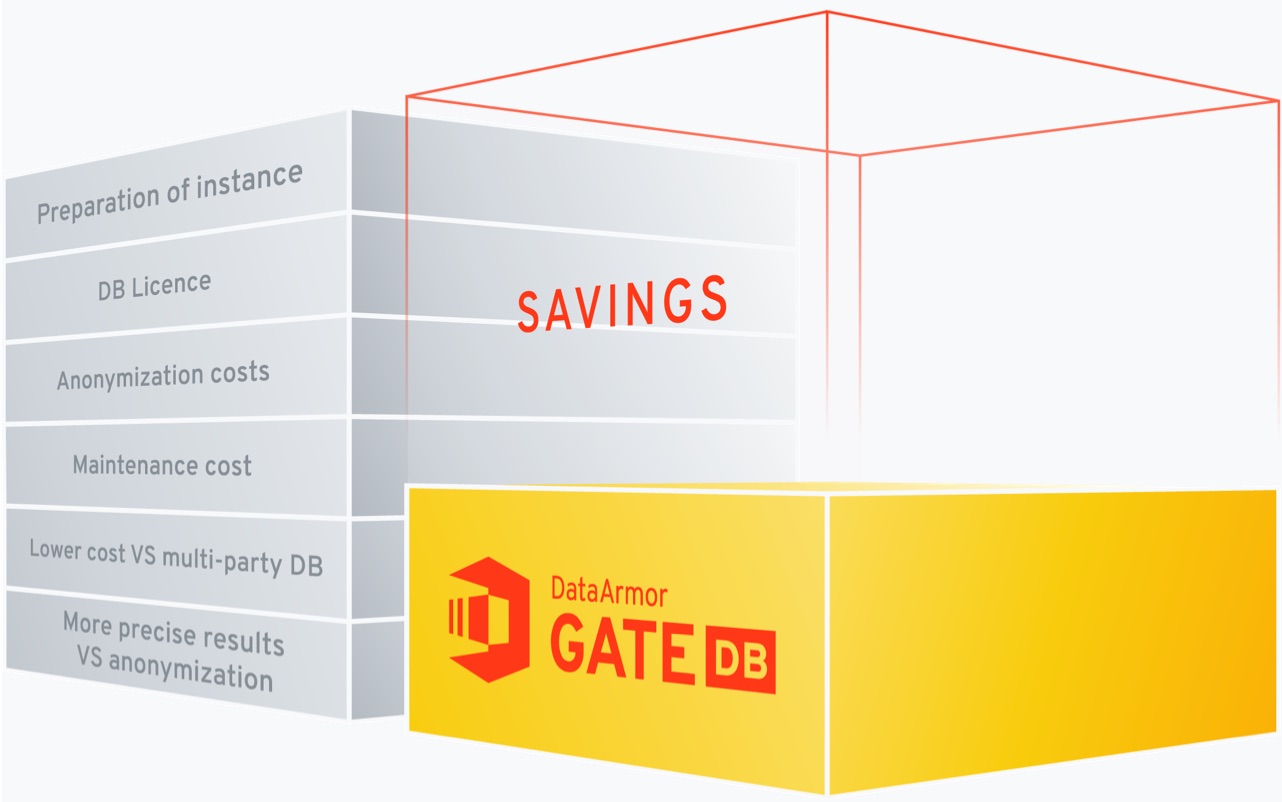
Easy and low cost introduction
No infrastructure replacement required, low integration costs
Allowing for the usage and storage of sensitive data in non-trusted zones such as the cloud.

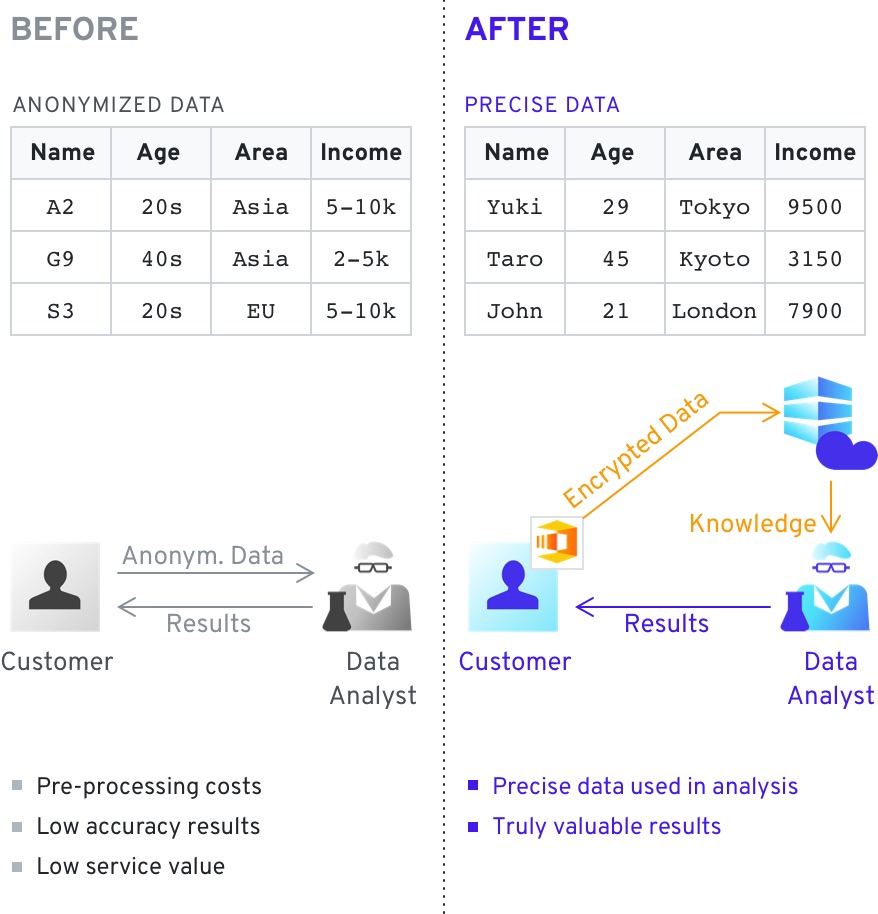
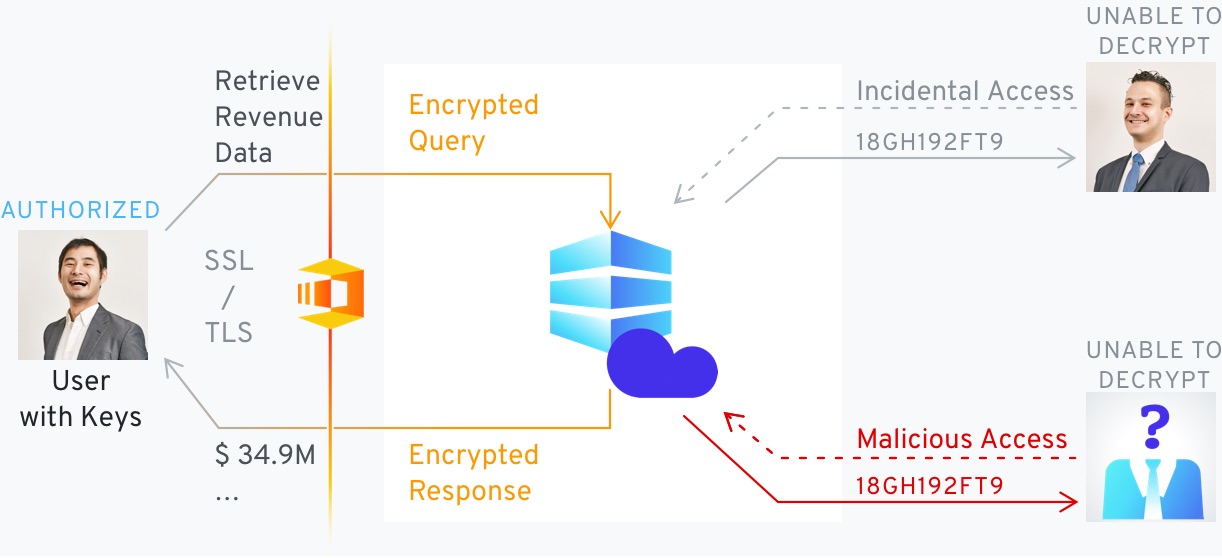
As the keys are not stored with the database you can rest assured that even if the data is compromised, it will not be decrypted. You can exchange, and gain access to, the overall knowledge of multiple datasets while keeping the details confidential.
Encrypting specific data subjects with different keys allows you to exchange data without revealing the information therein. You can gain access to the overall knowledge of multiple datasets while keeping the details confidential.
While 3rd party cloud resources may not always be implicitly trusted, our underlying technologies allow you to perform operations over encrypted data, and enable processing without any access to the raw information. This allows you to take advantage of lower cost cloud resources without compromising safety.

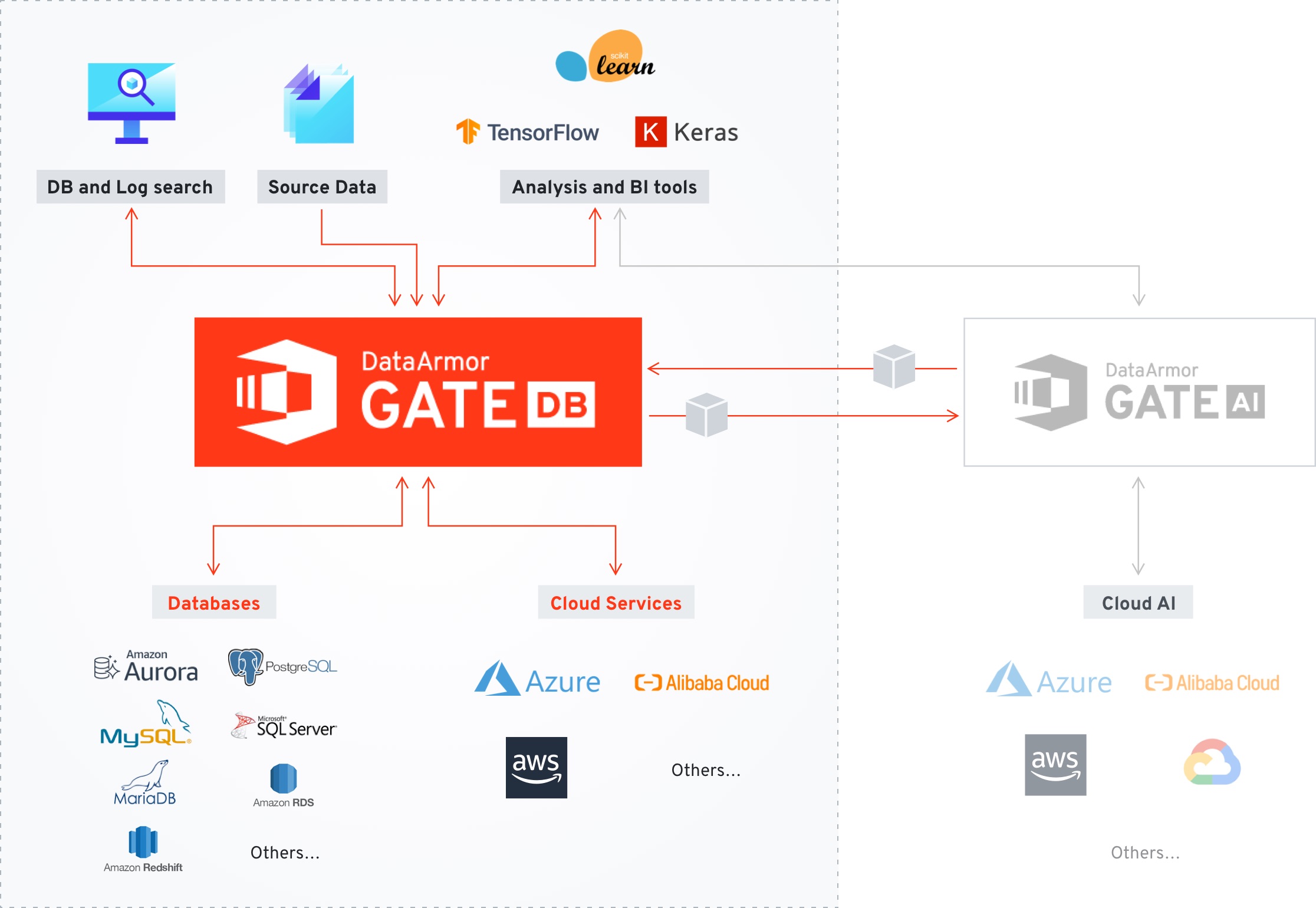
Eaglys’ DataArmor GateDB can be easlily Integrated with various popular services.
DataArmor Gate DB is a turn key solution for always on encryption of databases that contain highly sensitive data or operate in non-trusted zones such as the cloud. The contents of the database are always encrypted and all queries are performed over encrypted data only. The encryption keys are stored separately from the database, and data is never decrypted at the database side. This is in contrast to current database solutions which partially decrypt the data when performing queries.
We offer DataArmor Gate as a licensed product for deployment on premises, in the cloud, as well as offer consulting on projects incorporating the software into your existing environments. As the software is deployed in a docker image it is easy and quick to set up and get running. DataArmor Gate is agnostic with respect to the environments it runs on and can be used with various cloud providers as well as with various databases. Please contact us if you have any additional questions.

No infrastructure replacement required, low integration costs

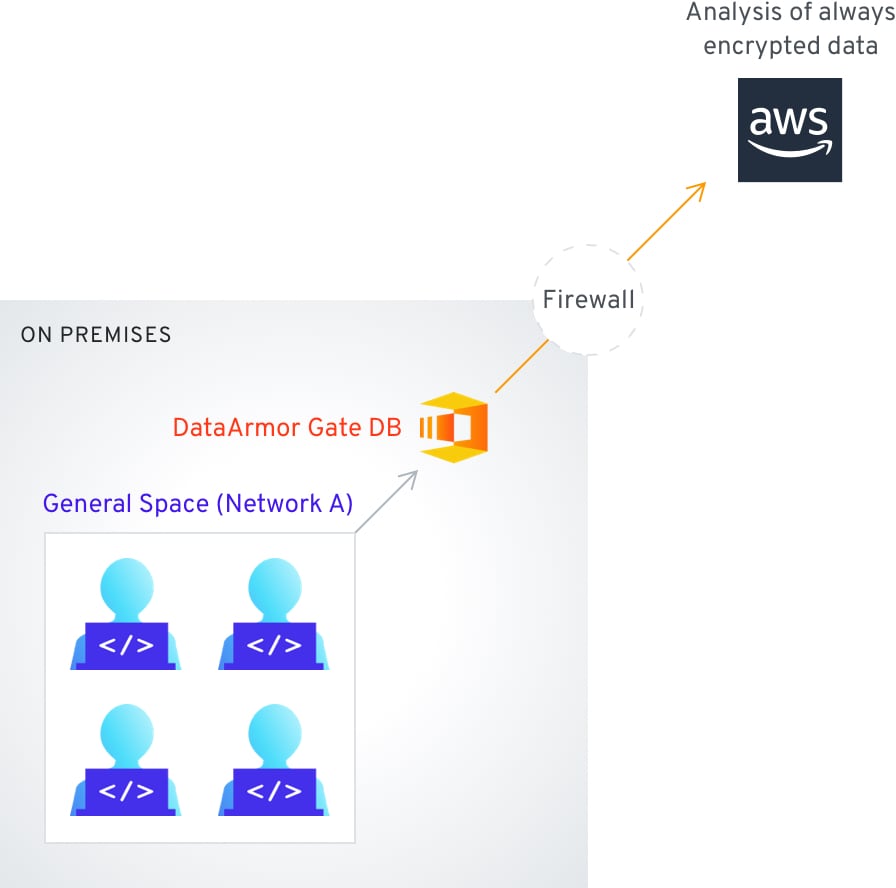
Flexible installation according to your security policy and network environment
High compatibility with third-party DB and your choice of cloud products
Discover the different scenarios in which EAGLYS’ DataArmor solutions can revolutionize industries and businesses that work with data.
The analysis of very sensitive data may require additional security and access controls, as well as prevent full use of cloud computing. However, with the use of secure computing the data can be stored off-site while the keys can be tightly controlled on-site. This allows for a stricter access control via key management, as well as obviates some of the need for additional parallel systems to store and handle said confidential data during analysis.
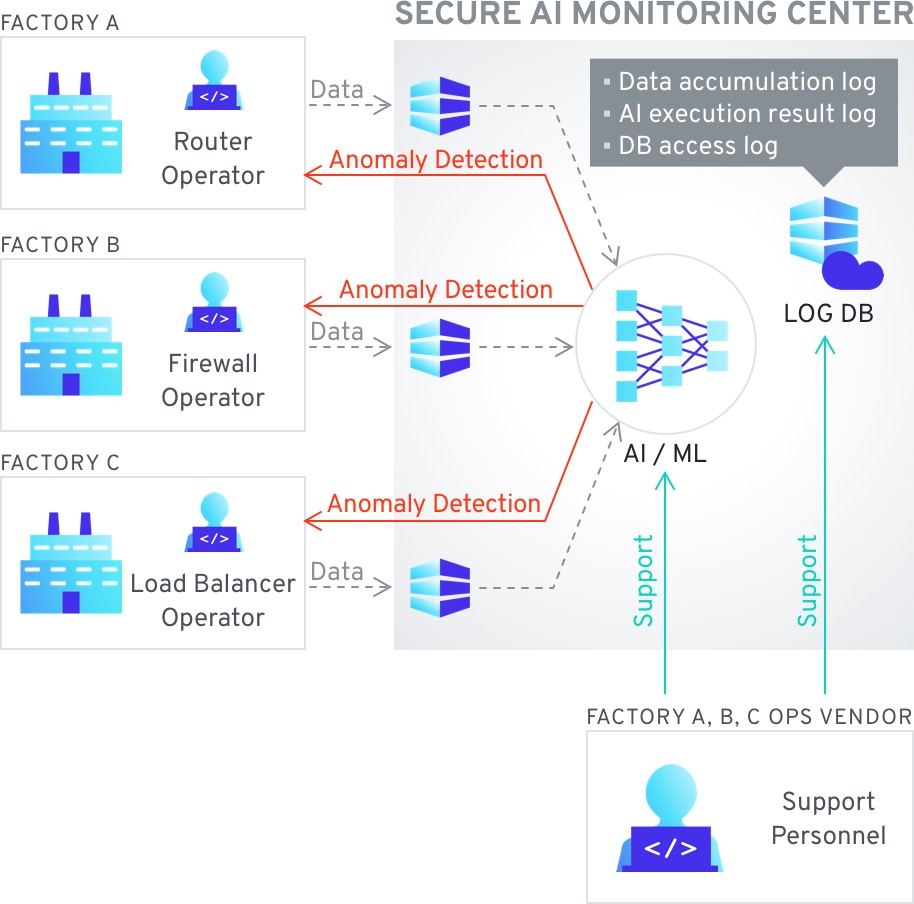
This use case concerns manufacturing statistical data, sourced from automation systems or IoT systems within the factory, providing information on performance, production output, logistics, etc. This data might need to be useable within the factory For any system that has to analyze and adjust operations autonomously. The specific drivers of this use case are security of the data in cases where the factory may not be in a completely Secure area, or the staff at the factory must not have access to detailed information – while the automated system needs the ability to calculate said data. One example of problems caused by access by wrong parties is the potential to predict the performance of a company ahead of earnings reports based on factory performance data.
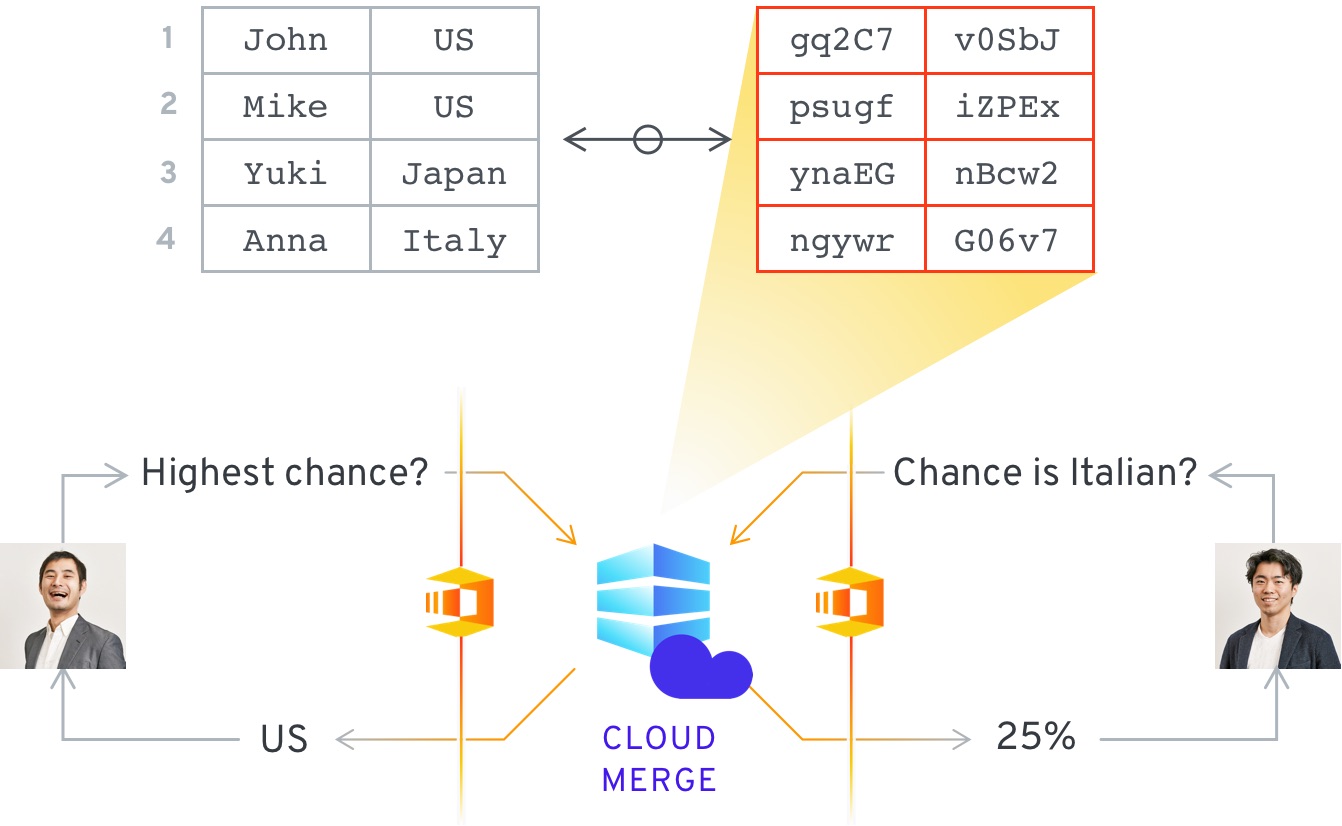
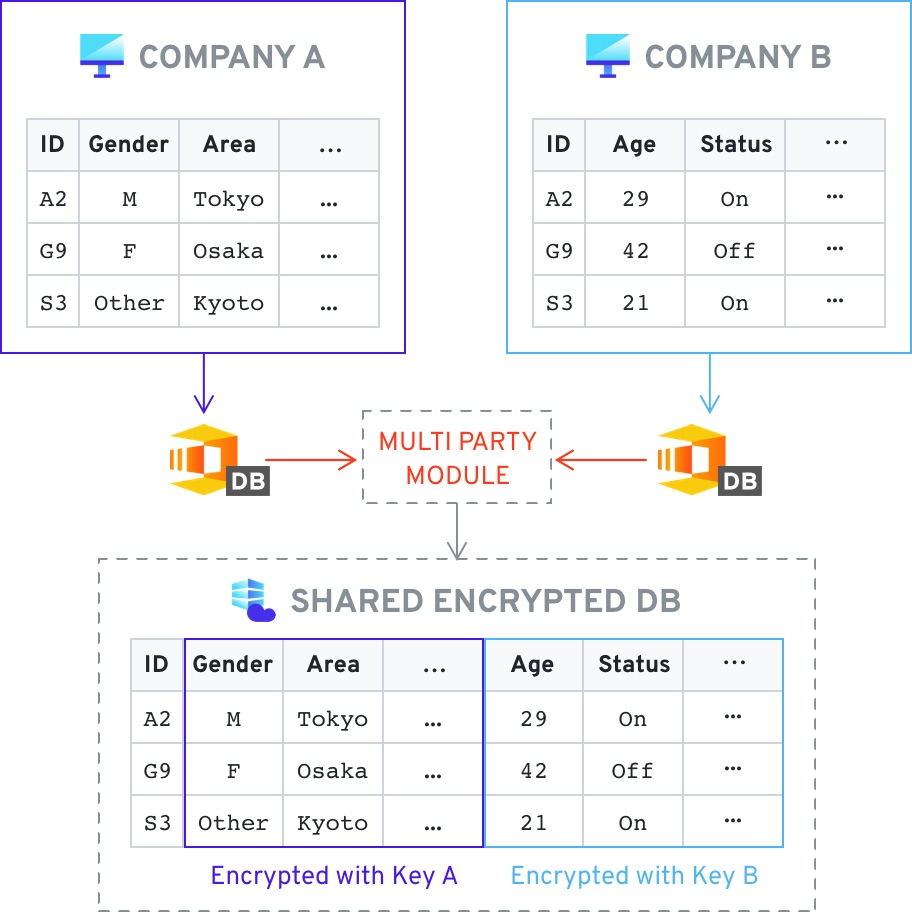
In this use case two different data sets can be merged using two separate keys, and stored in a central location, for example the cloud. Once the data is combined the entities can analyze the combined data without revealing the underlying information. This is extremely useful in cases such as fraud detection, where companies want to be able to analyze customer data for fraudulent activity, specific behavior patterns, or other flags - all without revealing the specific customer entries.
Each DataArmor Gate DB does not allow other parties (even platformer) to access its data inside.
Each decryption key is only used in its specific DatarArmor GateDB and no other party can know or access it.
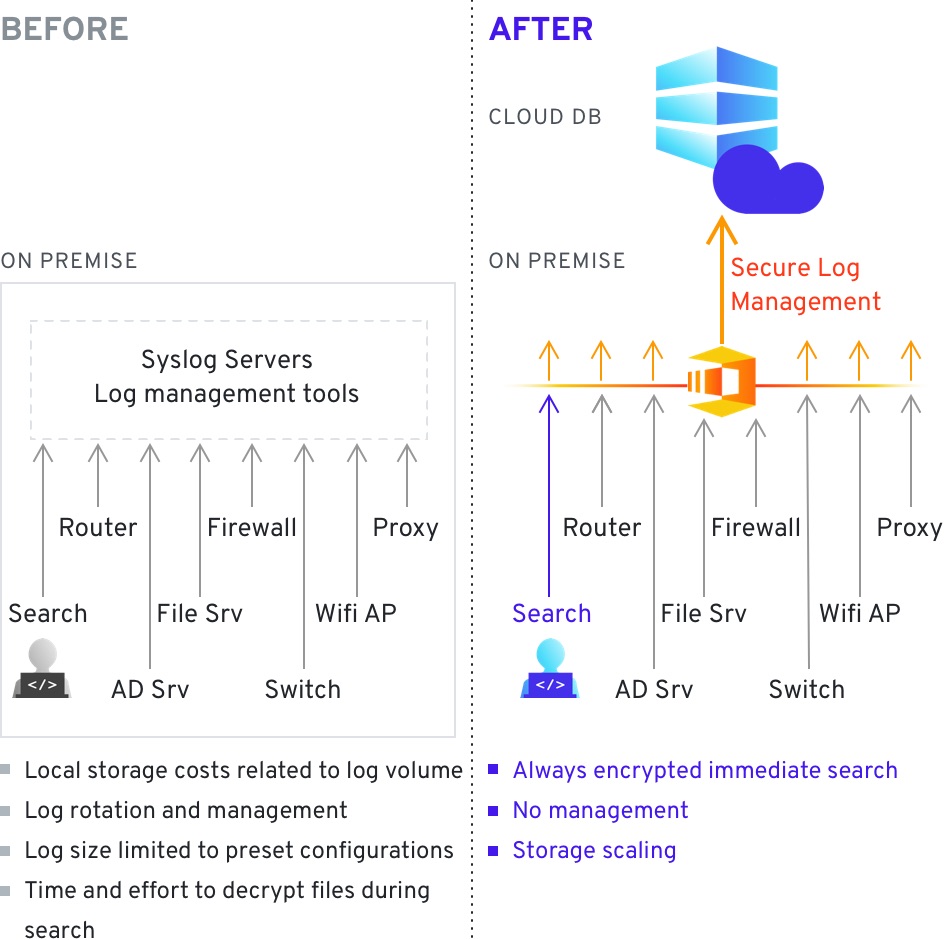
Secure computing can help in the aggregation of logs from various systems and IoT devices – as any system can encrypt and upload data into the cloud, without the possibility of the cloud service provider having any access to the data itself. While the data cannot be decrypted in the cloud it can be analyzed and transformed – allowing for the use of cloud computing resources and storage for sensitive log data while guaranteeing safety and confidentiality. This is especially important in cases where data needs to be centralized but logs may contain private or sensitive information such as account numbers, credit card numbers, etc. With secure computing both the ease of use and the confidentiality of the data is taken into account.
In cases where sensitive Human Resources information is outsourced to a vendor, data would often need to be obfuscated due to regulations and privacy considerations. However, with secure computing the data can be provided as an encrypted blob – completely unreadable however still allowing the 3rd party to perform analysis and apply specific computations as needed. Both the original and the resultant data is always encrypted and the 3rd party never has access to the underlying information – however their ability to fulfill their obligations is preserved.